
In today’s digital age, cybersecurity threats like DNS poisoning hacking attacks are a growing concern. These attacks manipulate the Domain Name System (DNS), a critical component of the internet, to redirect users to malicious websites. This blog dives into what DNS poisoning is, how hackers exploit it, and practical steps to safeguard yourself. Our goal is purely educational, raising awareness about this threat to help you stay secure online. Let’s explore the ins and outs of DNS poisoning and why it’s a serious cybersecurity issue.
What is DNS and Why Does It Matter?
The Domain Name System (DNS) is like the internet’s phonebook. It translates human-readable domain names (e.g., www.google.com) into IP addresses (e.g., 172.217.167.68) that computers use to locate websites. When you type a URL into your browser, a DNS server resolves it to the correct IP address, ensuring you land on the intended site. Without DNS, navigating the internet would be a nightmare of memorizing numerical addresses.
However, this system’s importance makes it a prime target for hackers. A DNS poisoning hacking attack (also called DNS spoofing) occurs when attackers corrupt DNS data, tricking your device into connecting to fake websites designed to steal data or spread malware.
How Does a DNS Poisoning Hacking Attack Work?
Hackers exploit vulnerabilities in DNS servers or networks to carry out a DNS poisoning hacking attack. Here’s a simplified breakdown of their tactics:
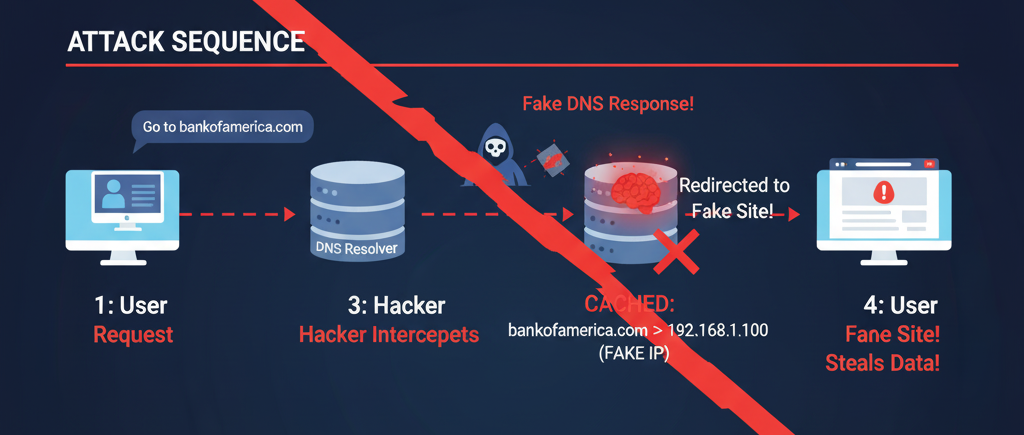
- Compromising DNS Cache: Hackers inject false DNS records into a DNS server’s cache. When users request a website, the poisoned cache redirects them to a malicious IP address instead of the legitimate one.
- Man-in-the-Middle Attacks: Attackers intercept DNS queries between your device and the DNS server, substituting fake responses to point you to their fraudulent site.
- Exploiting Weaknesses: Outdated DNS server software or misconfigured networks make it easier for hackers to manipulate DNS entries.
- Fake Websites: Once redirected, you might land on a phishing site mimicking your bank or email provider, designed to steal login credentials, financial details, or install malware.
For example, you might type “yourbank.com” expecting to log into your account, but a DNS poisoning hacking attack could send you to a fake site that looks identical, capturing your sensitive information.
Why Are DNS Poisoning Attacks Dangerous?
The consequences of a DNS poisoning hacking attack can be severe for individuals and organizations:
- Data Theft: Hackers can harvest passwords, credit card numbers, or personal information entered on fake websites.
- Malware Distribution: Poisoned DNS can lead users to sites that automatically download ransomware or spyware.
- Financial Loss: Stolen credentials can result in unauthorized transactions or account takeovers.
- Reputation Damage: For businesses, a compromised DNS can erode customer trust if users are redirected to malicious sites.
Because DNS operates behind the scenes, users often don’t realize they’ve been redirected until it’s too late.
Real-World Examples of DNS Poisoning
DNS poisoning hacking attacks have made headlines in the past. In 2019, a large-scale DNS spoofing campaign targeted organizations in the Middle East, redirecting users to phishing sites to steal credentials. Similarly, vulnerabilities in home routers have been exploited to alter DNS settings, affecting thousands of users. These incidents highlight why understanding and preventing DNS poisoning hacking attacks is critical.
How to Protect Yourself from DNS Poisoning
Fortunately, you can take proactive steps to shield yourself from DNS poisoning hacking attacks:
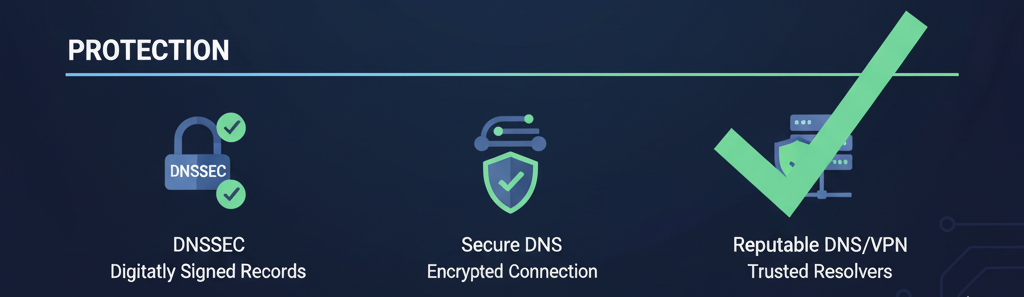
- Use Secure DNS Servers: Opt for reputable DNS providers like Google Public DNS (8.8.8.8) or Cloudflare (1.1.1.1), which prioritize security and encryption.
- Enable DNSSEC: Domain Name System Security Extensions (DNSSEC) validate DNS responses to ensure they haven’t been tampered with. Check if your ISP or DNS provider supports DNSSEC.
- Use a VPN: A Virtual Private Network encrypts your internet traffic, making it harder for hackers to intercept DNS queries.
- Update Software and Routers: Keep your devices, browsers, and routers updated to patch vulnerabilities that hackers exploit in DNS poisoning hacking attacks.
- Be Cautious of Phishing: Always verify website URLs and avoid clicking suspicious links. Look for “https://” and a padlock icon to ensure a secure connection.
- Monitor Network Settings: Regularly check your router’s DNS settings to ensure they haven’t been altered to point to malicious servers.
For Organizations: Strengthening DNS Security
Businesses face heightened risks from DNS poisoning hacking attacks due to their larger attack surface. Implement these measures:
- Deploy intrusion detection systems to monitor for suspicious DNS activity.
- Regularly audit DNS server configurations and logs.
- Train employees to recognize phishing attempts that may stem from DNS spoofing.
- Use enterprise-grade DNS solutions with advanced threat protection.
Ethical Reminder: Stay Legal
This blog is for educational purposes only. Unauthorized hacking, including DNS poisoning hacking attacks, is illegal and can lead to severe legal consequences. Always pursue ethical ways to learn about cybersecurity, such as certifications (e.g., CEH, CompTIA Security+) or bug bounty programs. Knowledge is power—use it responsibly to protect, not harm.
Conclusion
A DNS poisoning hacking attack is a stealthy and dangerous cybersecurity threat that can redirect you to malicious websites without your knowledge. By understanding how these attacks work and taking preventive measures like using secure DNS servers, enabling DNSSEC, and staying vigilant, you can significantly reduce your risk. Stay informed, keep your systems updated, and browse safely to protect yourself from the perils of DNS spoofing.
Have you ever encountered a suspicious website redirect? Share your thoughts or questions in the comments below, and let’s keep the conversation going about staying secure online!




